What would happen if a cyber criminal attempted to scam a security professional ? Well, some time ago, this happened to me. Like everyone, I certainly receive my fair share of junk email, scams, and pretty much everything else that the internet these days tends to throw at you. For the most part, each one of these “attacks” is ignored. However, one caught my eye after only the first paragraph. Not only was the format used absurd, but the supposedly “formal tone” was nothing short of a complete joke. Unfortunately, there really is no “TL;DR” synopsis for this particular event.
Scrolling to the bottom of the article is of course up to you, but you’ll not only miss out on key information - you’ll also miss out on my sarcasm 
Admittedly, this “scam” sounds far fetched. But, believe it or not, this particular campaign has a high success rate (and, all content in this article actually happened). If this were not the case, would a potential criminal go to such lengths to impersonate and engage ? No. They rely on that one human trait known as trust. Trust which in this case is readily exploited. I promise that this article will be worth your while reading. Ready ? Buckle up. its going to be an interesting ride. During the journey, I’ll highlight the warning signs and provide an explanation into each. Let’s start.
Day 1
Out of the blue, I was contacted via email by someone calling themselves “Andrew Walter” - purportedly an employee at Bank of America. The first immediate sign that something is not quite all it seems here is that the email address used is in fact from the contact form on this site. What’s significant about that ? Well, there are a variety of techniques used by cyber criminals to gain access to legitimate email addresses. One known and widely used technique is the scraping of email addresses from websites and social media - in fact, the most notable is LinkedIn.
Despite its age and somewhat basic approach, it still works very well. Why didn’t I secure it ? Simple. The contact form on this site also doubles as a honeypot. You’d be surprised what lands in here - as this “campaign” did. For the record, Phenomlab does not retain any information from this contact form. The initial text in the email might have been relatively convincing if it hadn’t contained a ”glow in the dark” grammatical error within the first line. What I’m alluding to here is that the email may as well have arrived complete with sirens and flashing lights. Here’s a snapshot
Dear Mark Cutting. “I added you to my professional network in order to share a confidential proposal with you please contact me on my private email: andrewwalter411@gmail.com for briefing on proposal since i can not send attachment via linkedin”.
Actually, you didn’t. I received no such request. Let’s have a look at the initial baiting technique. Who writes an email using the full name of a person without addressing them in the business (or even personal for that fact) sense ? In addition, why would you wrap what you want to say in quotes ? Finally, “I can not send attachment via LinkedIn” - actually, I received two from trusted sources in the same platform a day earlier. This email was so cringe worthy, I thought it rude to not reply ?
Andrew, Can I ask what this is in relation to please ? Thanks
That’s the hook that a scammer needs. After this, the response is a lot more detailed as the criminal plays out the story. I’m going to highlight the areas of interest here as I go, and have attached the full text in order to keep this article sane.
I will start by saying thanks for your response…How is your family doing? I hope okay.
Good start. Make it look like you know me personally and commence with the pleasantries - even though you in fact know nothing about me, and, in reality, couldn’t care less.
My proposal is very important to me so please I want you to take the content of this mail very serious. All I want is an honest business transaction between us.
This is anything but honest
Day 2
First of all, I will start by introducing myself. My name is Andrew Walter, I am currently working with Bank of America. I have been working here for 17 years now, and I have a good working record with my bank.
That’s strange. According to the array of fake Andrew Walter (Bank of America) LinkedIn profiles, you’ve been there for 12 years. Did you step into a time machine and not tell anyone ? Perhaps you banged your head and lost 5 years in the process. What’s more than likely is that like most bad liars, you’ve lost track of what you told one person as oppose to the next. At least you tried to enforce a bit of trust with your statement around “I have a good working record with my bank”.
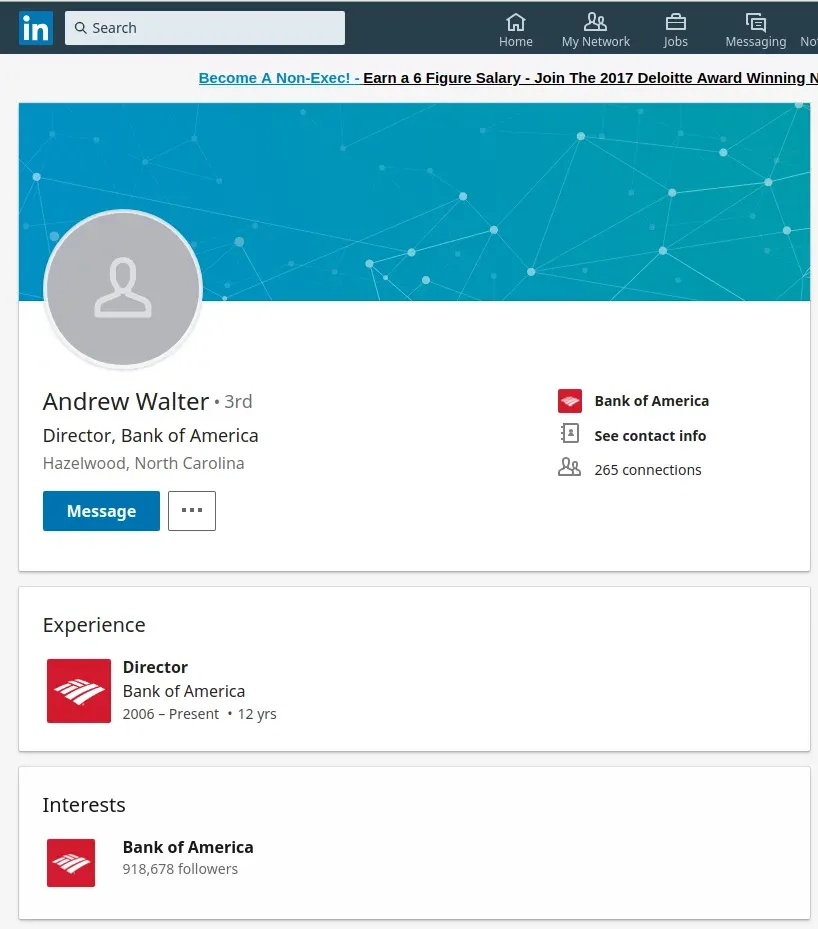

I am also the personal accountant to Engineer (Lex Cutting ), a foreign contractor who has an investment account with my bank with a huge sum of money in it.
Note the misplaced bracket here, and also note, that there is no “Lex Cutting” in my family tree. Am I a grammar snob ? No, but I expect a “business transaction” (if you can call it that) to at least not contain basic grammatical errors.
My late client was a chemical consultant contractor with Royal Dutch Shell until his death in a fatal car accident while at France on sabbatical with his entire family. The accident unfortunately took the lives of the family members comprising of himself, his wife and two kids in the summer of 2007 may their soul rest in perfect peace.
He banked with us here at Bank of America and had a very huge sum of money in his account which has still yet not been claimed by anybody as there was no living will in place when he died.
“May their soul rest in perfect peace” and “A very huge sum of money” - instant alarm bells owing to the poor grammar. If you’re working under the pretence of being an educated individual employed by a tier 1 bank, you’re not doing a very good job.
The amount of money involved here is about $15,812,664 (Fifteen Million, Eight Hundred and Twelve Thousand six hundred and sixty four US Dollars.) in account with indefinite interest.
Holy s***, I’ve won the lottery !! Contain yourself man, and remember, its a fake ! Ok, composure resumed.
Since the death of my client; my bank and I have made several inquiries to his embassy to locate any of his extended family members or relatives but this has proven unsuccessful. I came to know about you in my search for a person who shares the same last name as my late client.
Yes - I and thousands of others no doubt. How lucky I’ve been selected for this “unique opportunity”.
employed the services of LinkedIn search solely for this purpose as I feel it would not have been the last wishes of my late client for his whole life work to be transferred to a government (Es cheat) he had always complained of their unfavorable public monetary policies, taxes and so on while he was alive.
Ok, so let me get this straight. You’ve trawled LinkedIn looking for “beneficiaries” when there are other far more orthodox and reliable channels to obtain this information. I can smell the sweat and toil of poorly conducted fraud here. Oh, and by the way, “Es cheat” is actually one word (ESCHEAT).
My bank has issued me several notices to provide the next of kin or the account risk been es cheat within the next 10 official working days. The last notice for claim came to my desk last week. I am contacting you to assist me in repatriating the funds left behind before they are declared un-serviced by my bank. I am seeking your consent to present you as the next of kin of my late client since you share and bear the same last name.
As such, the proceeds of the account can be paid to you as soon as you contact my bank and apply for the funds to be released to you as the next of kin. If we can be of one accord, I see no reason why we would not succeed. We both have to act swiftly on this matter in other to beat the deadline es cheat date.Please get back to me immediately for us to proceed.
Wait a minute. If I’m the sole beneficiary, why do you want half ? Sounds like easy money to me. And the usage of “one accord” is somewhat “odd”.
I am after the success of this transaction with your full co-operation. All I require is your honesty and full co-operation to enable us see this cool deal go through.
I bet you are. “Cool deal” ? I thought I was taking to a professional here, not a school kid. Seems like our man has let his guard down for a split second and now his “Inna Gangsta” is shining through.
I guarantee you that this will be executed under a legitimate arrangement that will protect you and me from breaching USA laws. I want to also inform you that I am a very religious person and I cannot tell a lie because of my strong believes; I would expect the same from you.
Oh please, do me a favour. Pull the other one - its got bells on.
I will attach a copy of my international passport in my next mail for authenticity so we have equal ground to trust each other. If you are interested in my proposal I will send you more information directing you on further procedure on how we can claim the money in the account successfully. If this proposal is alright by you then kindly get back to me.
“Alright by you” - there’s that superb [sic] usage of business language again. This guy is awesome.
The content of this mail should be treated with utmost confidentiality and a quick response from you will be highly appreciated. However, if you are not interested in this proposal, please accept my apologies for sending you the message and kindly delete message, I promised that you will never hear from me. I anticipate your co-operation.
Of course. You wouldn’t want local law enforcement or the ”feds” knocking at your door now, would you ?
Day 3
This by now is so hilarious that I just had to respond.
Hi. This sounds great. What would the next steps be ? Eagerly awaiting your response.
And, without delay, here’s the response
Dear Mark Cutting. I thank you for responding to my mail, I want to stress again that this transaction is very legitimate and there is no risk involved as I am the personal accountant to Late Engineer (Lex Cutting ) anything I say concerning this will be followed by the bank Executives.
I bet. Actually, I’m struggling to follow your appallingly bad grammar here, but I expect you have your “very legitimate” reasons.
However, before we can proceed further, I want you to assure me that you will be honest during the transaction and as soon as the funds is transferred to you we can meet in person and share money peacefully. You should understand that this transaction can be successful if we work together and as soon as I give you all legal procedure you will receive the funds from my bank, so I really need your assurance before we shall proceed.
Wait - you want me to be honest ? Who’s scamming who here ?? What a complete scumbag.
As I read your email I am very convinced with you and serious about this arrangement process as such, I would want you to take this serious too. My personal instinct directed me to contact you and I hope it was not a wrong thing to do.I shall direct you on the process of the claim; we shall start by sending a formal application to this effect. I will send you the text for the claims and transfer application to this effect. Thereafter, the bank will request of you the relevant back up documents to your claim and application according to the demand of our probate law for transfer of funds.
Once you have provided the Bank with their demands, they would now be under legal obligation to transfer the funds to bank account provided by you. As part of the procedure of the claims, the documents that will be required from you will have to be acquired through legal procedures as the application of claim will be complimented with a legal award we shall have to seek from our law Court here. Be assured that the procedures to be adopted in effecting the transfer in your favor will be official and legal which will protect us from any breach of the law, We have the next 10 official working days.
Right. Sounds fairly “straightforward”.
Note: High confidentiality is required at all times. Do not tell anyone about this because, it might be unsafe for both of us. It would be safer for us to communicate by email for now as we have the trust. I hope you see reason with my decision on us talking by mail for now. As soon as the money has been transferred to your account, I will look for a country of our choice where we can see in person and subsequently share the funds in the ratio as discussed earlier.
I can assure you it won’t be unsafe for me, but it probably is for you -“…now we have the trust”. Note, that the scammer gains confidence here, and starts making some fairly basic mistakes.
Above all, I personally count on God to facilitate our plan and understanding, to produce not just success but also peaceful sharing of the funds at the end of the day and a wealthy family business relationship between us. I also pray for establishment of cordial relationship between us, God being our helper.
I agree - you’re definitely going to need all the help you can get here. You’re not getting anything from me, so divine intervention is probably the only thing you have left.
As soon as I hear from you and receive your assurance, I will send you the Text of Application for you to contact my bank for the release of the funds in the account of (Lex Nicholl) to your account as his next of kin.
Hold it right there ! Who is Lex** “Nicholl”** ? Major alarm bells here. Looks like this guy has his wires crossed or didn’t get good morning injection of caffeine. This is a glaring oversight and I’m guessing all those lovingly created campaigns have a similar fault.
would advice that you follow all the steps and procedures which I will give you so that we can get to the end of this transaction quickly. I need you to send a copy of your international passport to me and I will send mine as soon as I receive your reply indicating understanding from both of us.
Of course. You need my passport. How undeniably stupid of me to think that you could complete this “transaction” without stealing the holy grail of personally identifiable documents in the process and using it like the gift that keeps giving for your other criminal campaigns (I sincerely hope they are better than this one).
Day 4
Time to turn up the heat a bit
Hi. Can you send me the claims transfer forms for review ? Thanks
This guy is like a dog on heat and he’s well and truly bitten this
Dear Mark Cutting. I hope you and your family are well am so sorry for my late response as i read your email I was convinced, and I want you to understand that I need proper confirmation as I states below to be more in assurance of doing this transaction with you. The documents that will be required from us will have to be acquired through legal procedures as I explained, the application of claim will be complimented with a legal back up confirming this as a legitimate transaction, I have the account details with all access codes and will give it to you once it is required by the bank, also with me here all approvals will be provided and the transfer released to you.
We are going to keep our communication on email for now to ensure that we are under absolute security due to high level call interception here in United States I would like you to see it with me that security is very necessary we have to be on email or text messages until the transaction is completed and I will visit you to implement our sharing.
Yes, I agree that security is “very necessary” and also appreciate you do not want roughing up by “the feds” anytime soon. Let’s keep the communication on email so I don’t start to question who you are ? A quick side note here - if you want a secure channel, email is completely the opposite unless its been encrypted - which this hasn’t, and could be subject to eavesdropping. And, as a way of putting my mind at rest, here’s a lovely fake passport for your viewing pleasure. To the untrained eye, this could look convincing, but it a fake. One of the key identifiers here are the “wavy lines” over the picture. This is in fact a security watermark, and is unique for each passport issued. The lines will never repeat each other - if you look carefully at the below, the lines do in fact repeat.

Below is an actual fake passport that was used in a scam a number of years ago. You’ll notice that this one is slightly less complex as it has the watermark missing, but is still fake, nonetheless.

The transfer in your favor will be official and legal which will protect us from any breach of the law. Whatever the cost of his transaction will be, is going to be on both of us which I believe that you will not let me handle all the process alone.
Of course not. You wouldn’t want to have to share any of the spoils, would you ? And just like any other “business transaction” you don’t want to be spending any of your money unnecessarily. Interesting that he’s actually used the US English “favor” rather than the UK English of “favour”. Pity he’s not been so diligent elsewhere. I know…let’s try and spend mine.
I will give you the text application letter of the transfer request for our ledger department and also details on the way forward with the transaction once you have agreed with the following
-
Are you ready to maintain the high level of confidentiality required for the successful conclusion of this transaction?
-
Are you promising me that your account can be able to carry a transaction of such magnitude without any problem
-
Are you willing to accept 50% for your participation without any problems in collecting my share from you?
“Yes, yes, yes !” Let’s do this thing, and I’ll also throw in a portable radio to make the deal even more “appealing”.
I will need your help in directing me and investing part of my share in your country the investment will be under your control until I am able to take over or it can be a joint venture depending on your decision. as soon as i receive a copy of your passport or id document and i as well have attached a copy of my passport for you to see whom you are working with.
Please reply as soon as possible if you in understanding with me so that we can proceed with the bank with text application.
Day 5
Now this is getting interesting. What this really means is that once I have your bank details, I won’t be making a deposit - only a withdrawal (from my account, of course). Time to contact the Bank of America - this guy is an absolute riot (anagram of idiot) and yes, I can’t spell either, or count.
Dear Sirs, I write with reference to what I believe to be a 419 Nigerian scam, sent to my email address. I am a security expert by trade, and wish to report this to yourselves. I believe the “sender” is impersonating one of your employees. I have also enclosed a scanned PDF file of the “passport”, which I also believe to be fake. I’m currently entertaining this individual as a way of reeling him in so I can report him to the necessary authorities.
Clearly, I have no intention of supplying any sensitive information, including my passport. Whilst I expect that you receive many emails of this nature, I would like confirmation that the enclosed photo in the passport is not in fact a Bank of America employee
Sadly, absolutely no response from Bank of America. I expect that they receive thousands of emails like this on a regular basis. Oh well, onward and upward. Let’s not keep our friend waiting.
Hi Mark , Thank you for your email, and understanding, we do not have much time to complete this transaction to avoid reaching the es-cheat date.i will start the preparation of the application text which will be submitted to the bank as official application to cover the estate by the family member of Late Mr. Lex Cutting.
I will send it to you for review by tomorrow. As a side note, there’s that misplaced capital letter
Well now, that’s more like it ! Now we’re best friends forever, we can lower our guard a bit and revert to informal language (well, formal in the sense that our author is suffering from capital letter displacement). Perhaps we caused a bit of suspicion in our last messages and want to be a bit more convincing ? I’m game if you are buddy. Let’s make this a bit more interesting.
Hi Andrew, Thanks for the email. I’ve just moved house, and things are in a bit of a mess, so I cannot place my passport for a few days until I’ve finished unpacking - hopefully, this doesn’t cause you any problems. I can answer “yes” to all the questions below.
In the meantime, to speed up the process, is there any way we can proceed whilst I attempt to find my passport ?
Thanks
Well, look at me ! I know exactly where my passport is and I haven’t moved house - we need a bit of time here to do some further digging, so I’m throwing him off the scent for a few days whilst I perform some background investigation and analysis. I let this go on for 6 days before responding - note, that previously, “Andrew” had warned me we only had 10 days to nail this “cool deal”.
We’ve since passed that landmark, but interestingly, he’s not that worried it seems. Admittedly, at this point I thought of sending a copy of Jason Bourne’s passport which are readily available for download via a quick Google - http://www.indyprops.com/pp-bournepass.htm. However, despite my assumption that this person I’m dealing with is stupid, I don’t think there’s many people on this planet who haven’t heard of Jason Bourne or seen at least one movie from the franchise.
Based on this simple conclusion, its not a wise move in my view as it means ending the story here (unless this guy has been living under a rock)…. and there’s so much more to tell yet ! Therefore, we’ll need to take another route. Let’s increase the stakes. Note that by this point, we’re up to day 5, and we only had 10 days to complete this “cool deal”.
Its now day 11 after I’ve kept him waiting for 6 days intentionally.
Day 11
Hi Andrew, Sorry for the delay. I finally found my passport, and have scanned a copy. However, I’ve read that email isn’t secure, so I can either FedEx a copy to you (I’ll need an address of course), or I can provide a secure link for you to download a password protected zip file. I’ll email you the password for that under separate cover. Would this be ok ? Keen to get things moving. Thanks
I can almost hear the cogs in motion as my best friend formulates a response. A spanner in the works and probably not on his “canned response” sheet. This guy now needs to up his game to stay in the running.
Hi mark. I hope you and your family are well? thank you so much for your mail please scan and send the copy of your international passport to this email (andrewwalter166@gmail.com) will can communicate much better even while i’m right in my work place i can reply over there anytime. as soon i receive your reply we will be proceeding with the text of application.
I will be waiting to hear from you.
Yes, I bet you will. This is the response I expected (note the “new” email address highlighted in yellow above - why change this now ? Keep reading) - if I then dropped out afterwards, this guy would still have a copy of my genuine passport, and could (and undoubtedly would) use this to commit other types of fraudulent activity.
Essentially, its all about the money, so if the primary campaign fails, there is a good chance the second one will succeed, which is why the passport is requested so early to avoid over investment in terms of time.
Hi Andrew, I really don’t want to send my passport by email. Can you give me an address of where it can be sent (postal) or let me know if you’d be ok downloading the copy needed from a link I will provide ? Thanks
“Hang him on a hook and let me play with him”

I’m so bad. Let’s see how much he wants this. Pushing for the postal address risks blowing the (supposedly carefully planned) cover and exposing him. He can’t exactly give me an address in Africa now, can he ? I’ve already preempted this and laid the foundations for a honeypot trap. I need to explain myself a bit here for those reading this and scratching their heads with images of Winnie the Pooh and a honey jar, so bear with me.
A honeypot is a computer system or landing page that is set up to act as a decoy to lure fraudsters and cyber criminals - its essential function is to detect, deflect or study attempts to gain unauthorized access to information systems that are not for public use. At the heart of this honeypot is a system that is capable of obtaining a wealth of information about the accessing user in terms of IP address, geographic location, and a whole variety of data that would allow the recipient to piece together a trail of breadcrumbs. Any seasoned cyber criminal knows about the existence of such technology (its not exactly new) and would typically use a TOR browser to connect to any links provided by the victim in order to avoid detection.
The TOR network is a complex array of secured computer systems acting as “nodes” that traverse the internet using a variety of encryption mechanisms and connection masking, allowing the user to hide behind a number of random proxies that make it look as though he or she is accessing from a completely different geographical location. The TOR network was originally intended for use by the US navy, but found its way out and became the favourite watering hole for many a cyber criminal - and today, known as either the deep web, or worse, the dark web. Ok, that’s enough history and boring technical terms. Let’s get back on track. Essentially, I’ve created a hidden honeypot on this site and the only two people who have this link are myself, and our scammer friend. The page cannot be indexed or crawled by Google either. Time to up the stakes
Hi Andrew, Any update to this please ? Thanks
Day 12
No response. Perhaps I’ve pushed this a little too far. Let’s see
Hi Andrew, I’m concerned that I haven’t heard from you and don’t want to miss out on this amazing opportunity. Can you let me know what we need to do next please ? Thanks
I honestly thought that he wouldn’t reply, but he did.
Dear Mark Cutting. Hope all is fine with you and the family? i am writing to know if you are still interested with this transaction i need a copy of your international passport in other to know whom i’m working with for more verification as soon you send it down here
Now, when I went to school, the UK was across from America and not down - hence the term “across the pond”. Did I miss something here ? A figure of speech perhaps, but more likely a slip of the tongue. Looking at a map “down here” would indicate south, surely ?
we will be proceeding with the text of application to contact my bank for funds relic please update me as soon as possible.
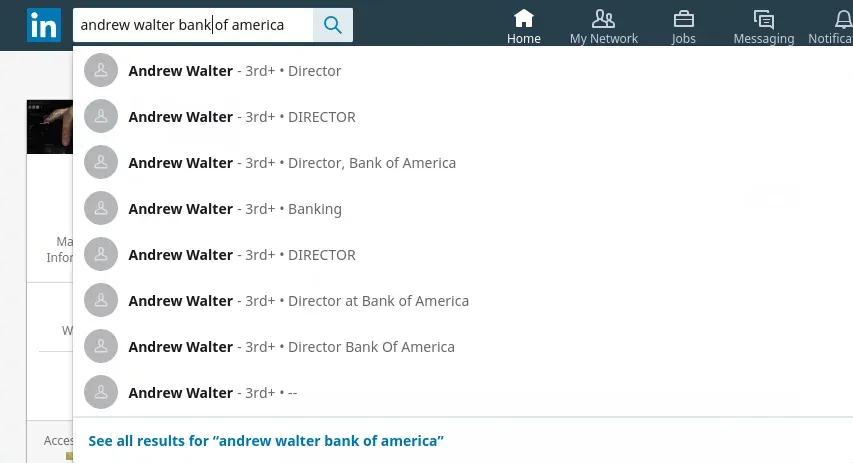
And here we have another schoolboy error. This guy thinks he can relax now he’s done his chore. Not only is the text clearly copied and pasted (with the formatting intact so he first line doesn’t match the rest in terms of font size), but much worse is the fact that he’s now using a different email address altogether and hasn’t even made any attempts to hide this. Clearly, he’s got a lot going on, and there are undoubtedly hundreds of “Andrew Walter” doppelgangers lurking in the shadows like something out of Michael Jackson’s “Thriller”.
To understand this complete failure, let’s take a closer look - perhaps he’s got some sort of “Salesforce(esque)” campaign on the go where willing participants are directed to another email address for easy reference (milking)! The email address we started with was “andrewwalter411@gmail.com” which in itself isn’t very convincing. Now we’ve suddenly switched to “andrewwalter166@gmail.com” and also lazy again with our grammar as “Andrew Walter” is now “andrew walter”.
I suppose I could send him a Starbucks voucher so he can get a strong coffee and wake up, but, this is his gig, so I’ll let him play his hand.
Hi Andrew, As I previously mentioned, I won’t send my passport via email because I was told it wasn’t secure. Instead, I’ll provide a link to a secure website where it can be downloaded as a zip file. I’ll also provide the password for the zip file so you can extract it. I’ll get this over to you today. Thanks
Now we’re “upping the ante” a bit. Not only do we respond to the original email, but also to the new one with the same message above. I’m relatively sure at this point that our friend isn’t exactly an experienced fraudster, and probably won’t even notice his own mistake. Wait for a bit……. then send the link. Note that the link itself has been redacted for obvious reasons and is not the original.
Dear Andrew, I’ve scanned a copy of my passport to PDF and placed it in a password protected ZIP file. It can be downloaded using the link below. https://[redacted]/KCXXu4MN8G6FZqFt4Mb7hQfRZXmHA3Fn/securedownload/ Let me know as soon as you’ve downloaded the ZIP file, and I’ll send you the password in a separate email. Thanks
I wasn’t really expecting this guy to bite if I’m being honest, but never say die - he’s just fallen straight into the honeypot (or should I say, “boiling pot”)
Hi, the link is infected i can not open it my system refused to run the link. send it via pdf which i can view before download or jpg.
Actually “Andrew”, the link **isn’t **infected. I understand your frustration though, as its very annoying having your time wasted by a moronic idiot who seems to lack the ability to string even basic sentences together…… Alright - that’s enough of that. The thing is “Andrew”, you didn’t follow my instructions. Not that this really matters at the moment anyway as I have got what I came for. The string on the carrot has just been made shorter. I know at this point, you can almost taste it, but I’m not finished with you just yet.
Hi Andrew, The link works fine on my PC. its a password protected ZIP file created by 7Zip. If you use this to extract, you’ll need to enter the password to extract the PDF which I’ll send you under separate cover. Regds
He’s in for a bit of a surprise when he gets around to opening that Zip file. There’s a PDF there all right, but it’s certainly not my passport. In fact, “Andrew” has had three attempts at downloading that file
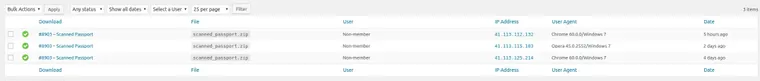
According to the honeypot, it would appear that he’s operating out of Randburg (Johannesburg, South Africa) - a very well known fraud hotspot.
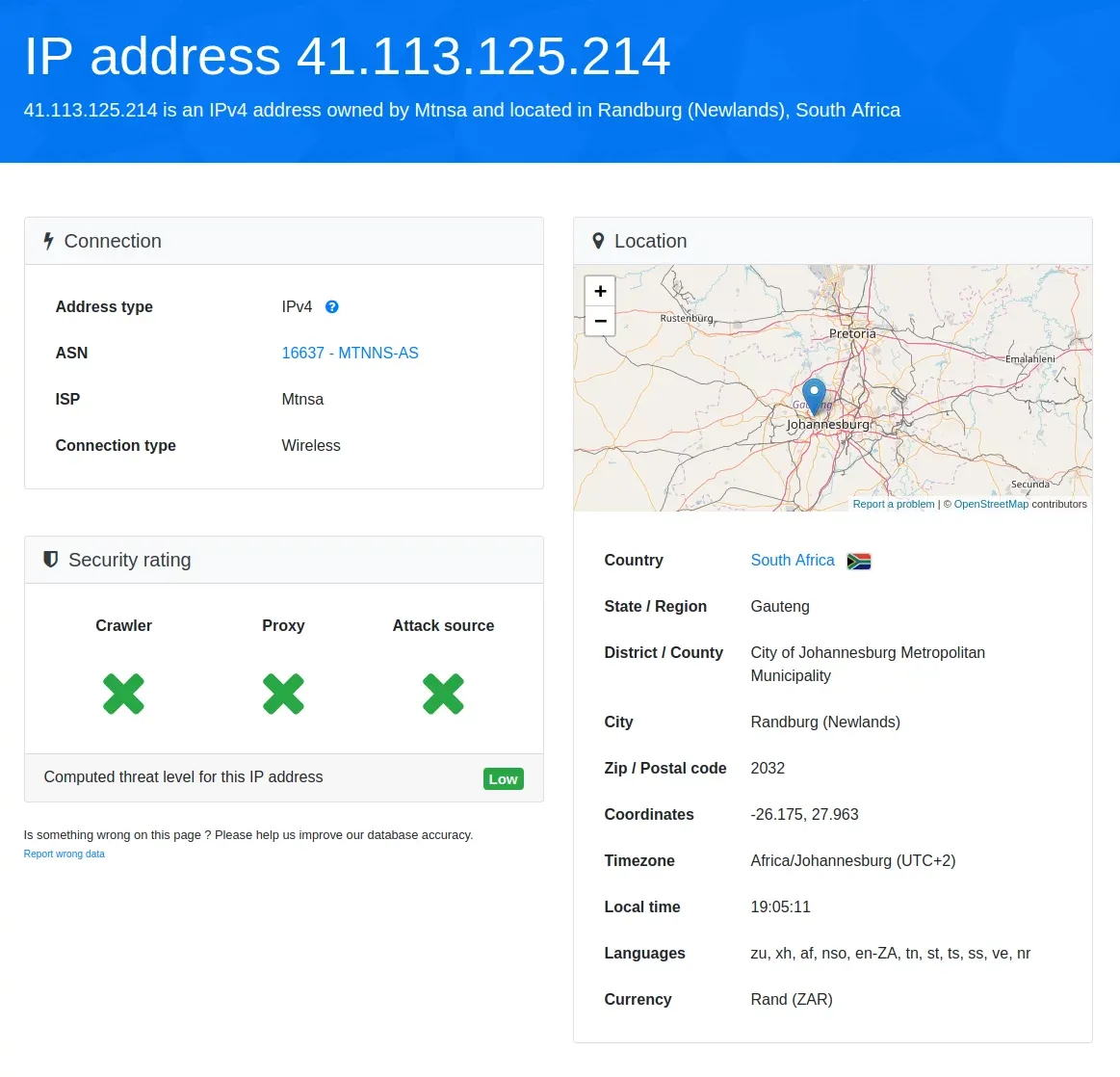
The GEO information is provided courtesy of https://db-ip.com/41.113.125.214
If those coordinates are accurate, then the local law enforcement aren’t too far away. Have a look below
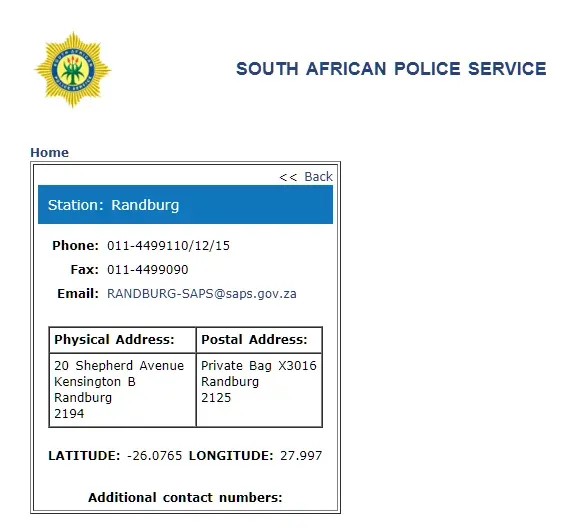
In fact, about 12 miles away (dependant on exact location of course, which the local ISP can provide when requested by law enforcement agencies)

Day 13
The next steps here are quite obvious. Pass it onto the local authorities to investigate, with a copy of all material received thus far
Dear Sirs, I write with reference to an incident where a scammer in your location has trawled LinkedIn and obtained my address with a view to commit coercion and fraudulent activity. The IP address that this fraud attempt has originated from is https://db-ip.com/41.113.125.214. I have a complete record of all activity, plus a copy of what I believe to be a stolen passport.
I am a security professional by trade, and wish to report this as criminal activity. I have a complete evidence chain of emails relating to this particular event - the incumbent has requested a copy of my passport (which for obvious reasons I will not be providing), and no doubt will also attempt to acquire my bank details. This person is posing as “Andrew Walter” from Bank of America - there are several fake profiles on LinkedIn relating to this individual. I am also aware that local law enforcement can request the physically connected location for this address - you should find its about 12 miles away from your location.
I have obtained this fraudster’s IP address via a honeypot on my website, which I purposely setup to extract this information. I would appreciate your cooperation in this individual’s apprehension, as it would appear that the same person is responsible for a number of similar campaigns designed to extract funds from others. I am based in the UK, but can be free to discuss as you deem fit. I have enclosed copies of all emails received so far, plus an example of the LinkedIn profiles which I believe are fake. Mark Cutting
And the below read receipt shows that this email has been read (well, opened, at least)
Your message was read on 16 May 2018 10:32:48 AM UTC. Final-recipient: RFC822; T0023694@saps.gov.za Disposition: automatic-action/MDN-sent-automatically; displayed X-MSExch-Correlation-Key: c1tMJuEijE6r4WJRtMhQlw== X-Display-Name: GPS:Randburg SC Admin
its at this point where things become much clearer. This guy really hasn’t done his homework. He’s been conversing with me outside of US time zones (well, Johannesburg is only currently 1 hour ahead of the UK after all) which can only mean he either has severe insomnia, or isn’t actually based in the USA. I wonder which one it could be ? Perhaps he should see a doctor and get some pills for that….  I’ve since sent “Andrew” another email, but unfortunately, he hasn’t replied. I guess he’s “busy” with his next victim.
I’ve since sent “Andrew” another email, but unfortunately, he hasn’t replied. I guess he’s “busy” with his next victim.
Hi Andrew,
I’m a bit concerned I’ve not heard from you, and with the deadline approaching, I really do not want to miss out. Can you let me know if you were able to open the zip file with 7zip as I previously mentioned ?
When you try to extract it, you’ll need a password which I’ll provide to you once you confirm you’re able to open.
Please keep me updated.
Thanks
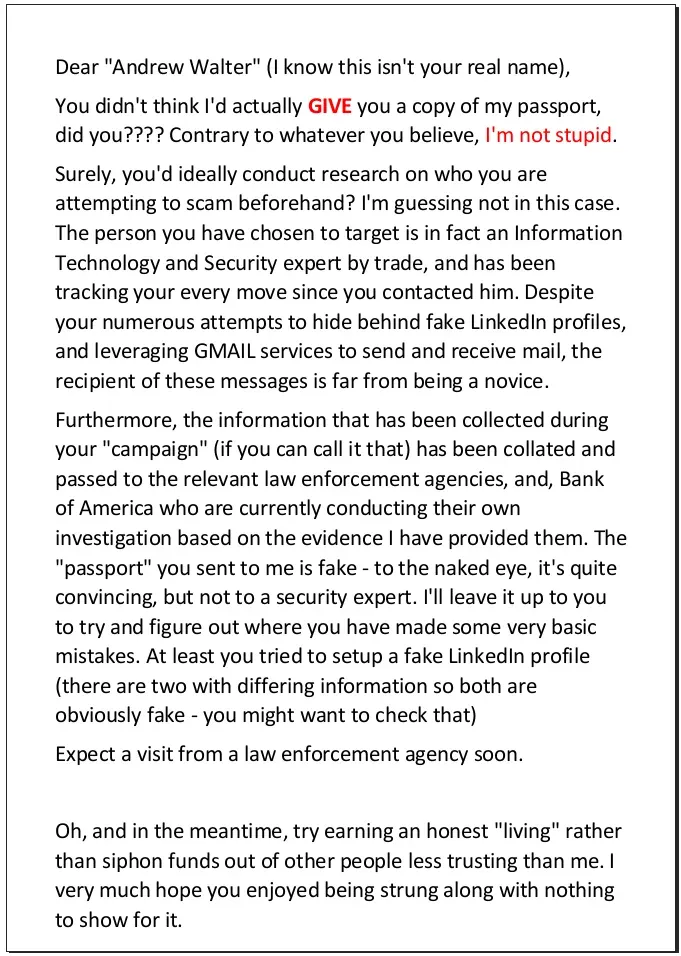
The ironic thing here is that “Andrew” in fact already has the password for that zip file I sent him ! If he’s the hotshot he makes out to be, then I’m sure he’ll work it out. In the meantime, I’m guessing you all want to know what that zip file contained ? Well, I did say it was a PDF, but its not my passport. Here you go.
Conclusion
Sadly, there’s been no response to the email I sent to SAPS (South African Police Services). Oh well. They have all the evidence they need, although in fact, no actual “fraud” has been committed. That effectively means that “scoping out” a potential victim and attempting to reel them in isn’t actually an offence. Although identity impersonation certainly is and I’d be surprised if they were not interested in this.
So there you have it - a walk-through of what to look for in these types of scam. Here’s the highlights
- No official institution like the Bank of America is going to allow its employees to conduct business over a GMAIL account.
- In all honesty, faking the bankofamerica.com domain would have been much more convincing, and wouldn’t have taken much effort either. After a quick iteration of the real name, I found the below
- If an email supposedly comes from the US, then why are all emails being sent outside of their working hours ?
- Any transaction of this sort would never be conducted over email anyway - for this amount (if this were indeed real), it would have to be completed face-to-face in the presence of bank officials, lawyers, compliance, and a whole raft of others.
- No institution is going to request a copy of any identifiable details (passport, bank accounts, etc.) over email.
- Poor grammar is an immediate warning sign. You need at least a decent grade in English if you are going to pretend to be someone you’re not
- Bad spelling is another. There are so many errors here and it makes any campaign stand up and shout “hey, I’m fake !”
Hope you enjoyed this somewhat absurd journey.
Keep safe out there, folks.












 I’ve since sent “Andrew” another email, but unfortunately, he hasn’t replied. I guess he’s “busy” with his next victim.
I’ve since sent “Andrew” another email, but unfortunately, he hasn’t replied. I guess he’s “busy” with his next victim.
